Encrypting files on your hard drive for safekeeping is all very well, but how can you share protected information with your family, friends, and colleagues without compromising data security? In this post I'll outline how to encrypt, transmit, and decrypt protected files safely using the Gnu Privacy Guard (GnuPG) program on Ubuntu.
GnuPG is installed as an integral part of Ubuntu during the installation process1 and it uses the embedded Passwords and Encryption Keys application as a GUI (also known as a front end) by default. The obvious and most frequent use for this program is to store and access system passwords but, when coupled with the Seahorse Decrypt File plugin, it also facilitates data encryption using twin encryption keys known as a keypair.
The first of these keys is the private key which the key owner uses for decrypting files encoded using his keypair. This key should never be revealed as anyone with access to it also has unfettered ability to read files encrypted with that keypair (assuming that an infiltrator has also acheived access to the files).
The second key of the pair is the public key which is used to encrypt data destined for the key owner. This public key may be distributed freely2 to anyone who might wish to send confidential information to the key owner.
As a simple illustration of the process, imagine two friends, Laura and John. John wants to send Laura a confidential file; both are using Ubuntu and have installed the Decrypt File plugin from the Ubuntu Software Centre:
- Laura creates a (or selects an existing) keypair.
- Laura Exports her public key to a text file3 and forwards it to John.
- John Imports Laura's public key and uses it to encrypt his file. He sends the encrypted copy of the file to Laura.
- Laura uses her private key and passphrase to decrypt the file.
Probably the easiest way to manage this process is to use the Passwords & Encryption Keys interface, but it can be managed equally well from the command line.
You can use these instructions to create your keypair or, if you have already created the keys, you can use an existing key. To Export a public key from the Passwords & Encryption Keys interface:
- Open the application (either from the Accessories menu or by typing
seahorse at a command prompt).
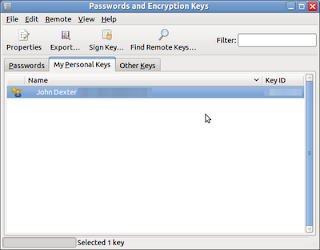
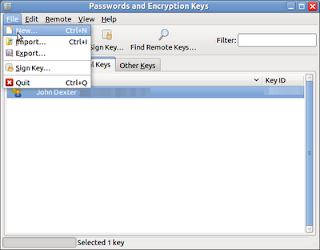
- Select the My Personal Keys tab and select the key that you want to export.
- Click File and then Export...
- The Export public key dialog appears - choose a name for the key and a location to store the text file. The default name is the Key Owner's name (including spaces and with the .asc file extension) and the default directory is the usr/home directory; however, you can amend these parameters (however, avoid changing the file extension) to suit your needs.
- Click Save
Exporting a public key from the command line is just as simple; open a terminal and, at the command prompt, type:
gpg --export -a -o "User Name.asc" [UID]
(See Note4)
The Key Owner can distribute the public key any number of ways, but to forward the key to a specific recipient, the text file can be attached to an email. Recipients of the key can simply double-click the file to import it to their Other Keys tab of the Passwords & Encryption Keys application5.
Importing a public key from the command line is also simple; from the command prompt, type:
gpg --import [Filename]
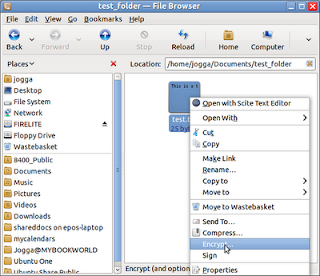
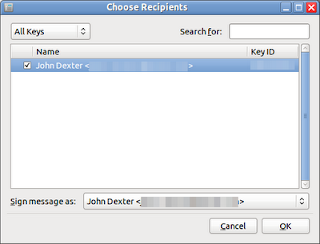
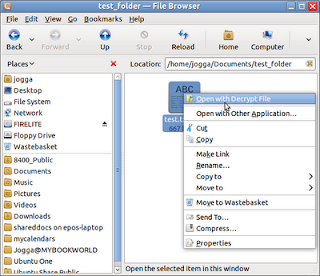
The File Owner can now encrypt the data by right-clicking the file in Nautilus and selecting Encrypt... from the pop-up menu. When the Choose Recipients dialog appears, the File Owner selects the appropriate key from the list and clicks OK. The encrypted file will be saved in the same directory as the original (with a .pgp file extension) and can be forwarded to the Key Owner.
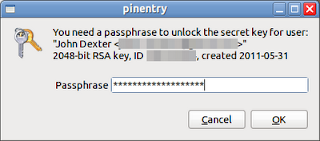
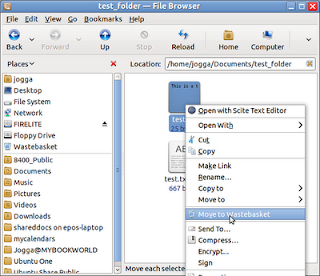
On reciept of the encrypted file, the Key Owner simply righ-clicks the file and selects the Open with Decrypt File option. The Key Owner will then be prompted for his or her passphrase (chosen when the keypair was created) and the file is decrypted.
Notes:
1 Ubuntu Documentation: Gnu Privacy Guard How To
2 So freely in fact, that many key owners publish their public keys on the internet in order to facilitate confidential exchanges.
3 Actually, the output from the Export process can also be in binary format (as it is by default from the command line) but for simplicity, I have stuck with ASCII formats.
4 Where:
gpg refers to the Gnu Privacy Program
--export is the command to export the public key
-a is the command to export the key in text format
-o prepares the command for the destination directory and file name
"User Name.asc" is the file name. The default is usually the key owner's name and quotation marks are required if you wish to include spaces in the file name. The default directory is usr/home/ but you can specify a full path in the command line (e.g. /usr/home/Documents/Keys/" ser Name.asc")
[UID] is the key identifier. To list the available keys from the command line, type
gpg --list-keys
or view the list of keys from the My Personal Keys tab of the Passwords & Encryption Keys application.
5 You can also save the file to disk and use the
Import... option in the
Passwords & Encryption Keys application: however, double-clicking the text file is easier!
Before running any application or invoking code, make sure that you trust the source!
Sources & References: